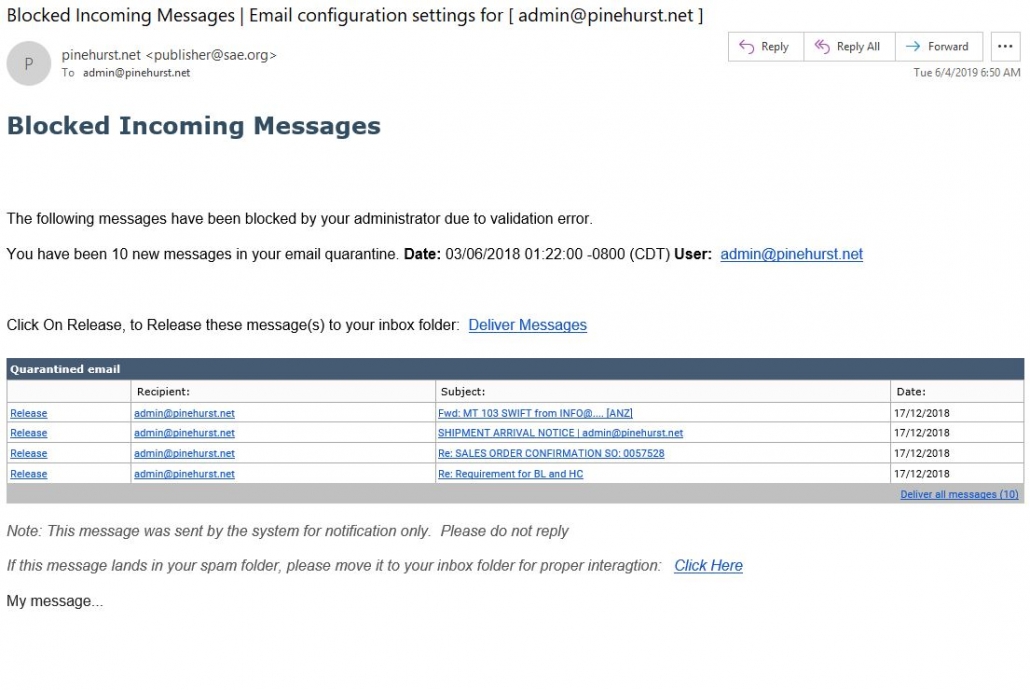
Fake Flash Update Warning
There’s a certain web site I’ve visited a few times that produces a fake flash update warning. Beware of these warnings. Adobe will never display a warning such as this when you’re surfing the web.
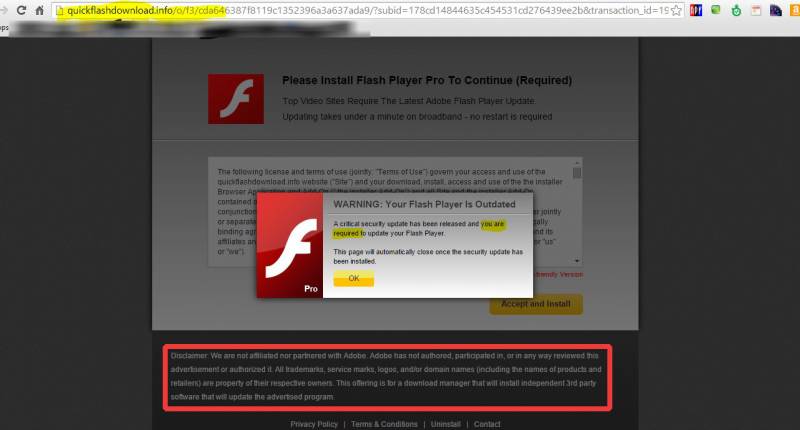
Here’s a screen capture.

First of all, I want to warn everyone never to click on anything like this without examining it first. There are three glaring examples of fakery to be found at a cursory examination.
#1 The URL has nothing to do with adobe.com.
#2 The message says that you are required to update your flash player. You are required to update nothing of the sort. As the saying goes, you are only required to die and pay taxes! Adobe (and other legitimate companies) will not generally display scary messages like this.
#3 This is the most important part… inside the red box, the advertiser says they are not affiliated with Adobe, the makers of Flash..
If you do accidentally click on the OK button, you will be asked to download or install something with a generic name, like “installer.exe.” Don’t do it! In my experience today, I clicked on nothing at all, and still got the download dialog box.
Well, now that you’ve determined you have detected a scam, what do you do? My advice is to close the browser. If you’re an inexperienced user, and you always seem to be getting malware, the best course of action is to go ahead and shutdown your computer without trying to click on anything at all. Press the Windows button on your keyboard to get to the start menu and click Shut down.
Be careful!
Note: I use both Windows PCs and Apple computers. I have only seen this happen on a Windows PC to date.







 Here’s something to look out for! Have you ever paid for something with PayPal and expected that to be the last of it, but you ended up on a recurring billing plan? Here’s how you can check to see what’s been preapproved or has been scheduled.
Here’s something to look out for! Have you ever paid for something with PayPal and expected that to be the last of it, but you ended up on a recurring billing plan? Here’s how you can check to see what’s been preapproved or has been scheduled.